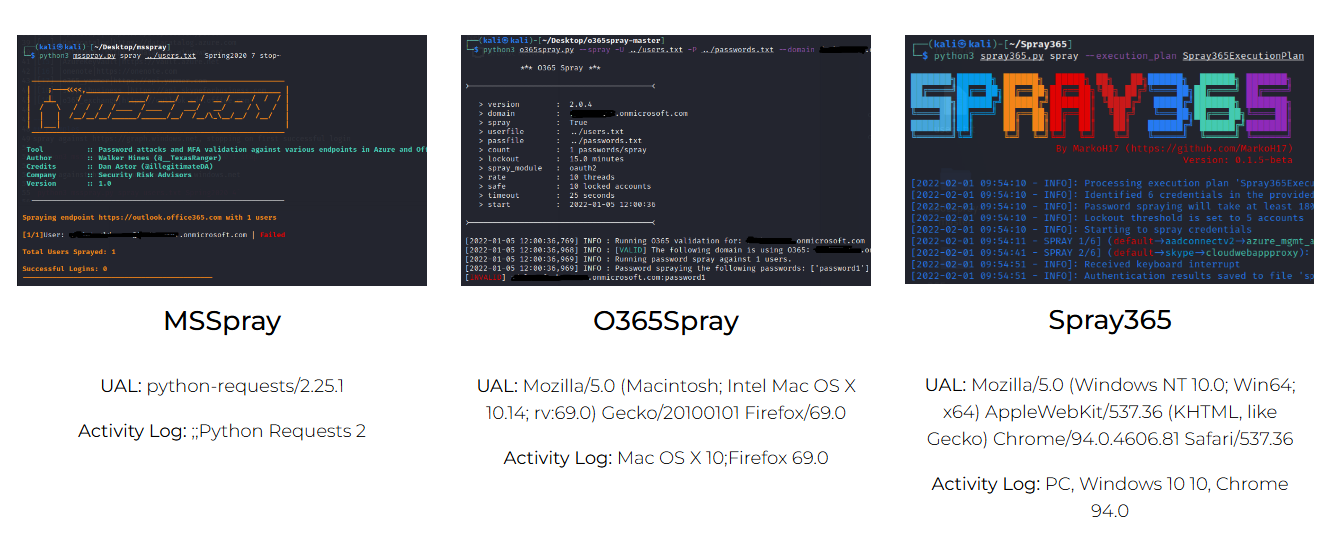
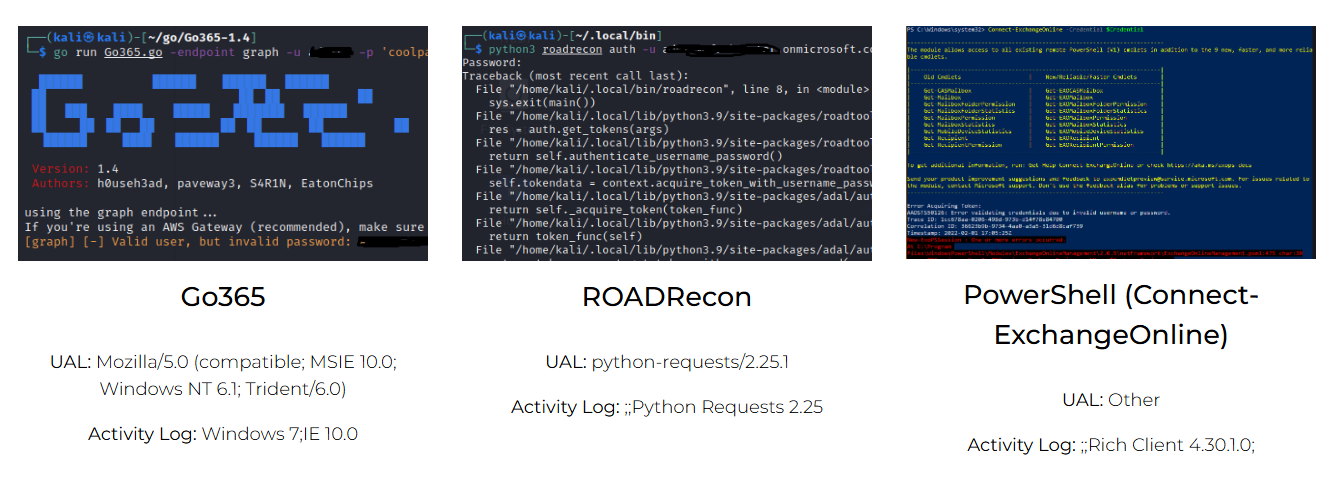
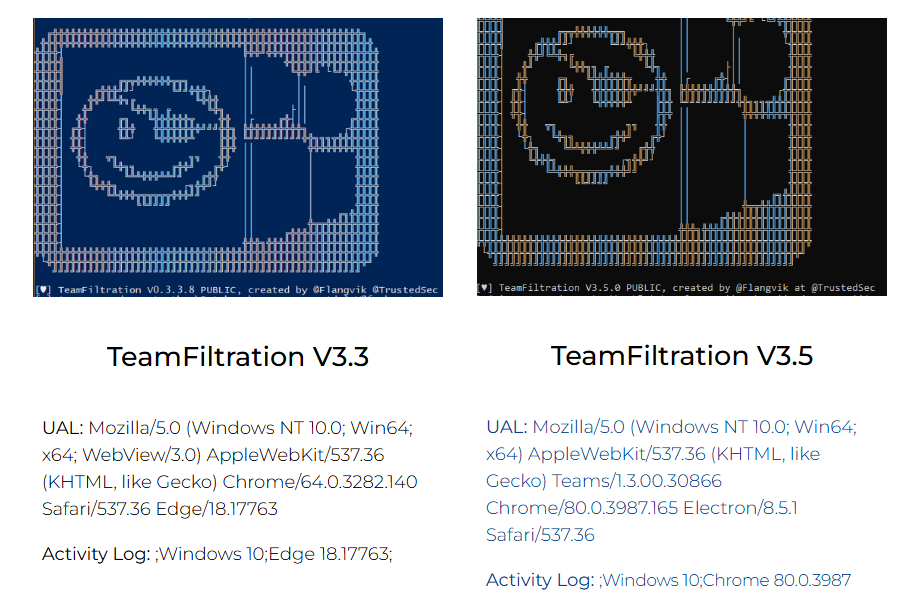
Microsoft 365: Attack Tool User Agents
There is no shortage of tools available for enumerating the users in a Microsoft 365 tenant (AKA Office365) and testing password security. But what do these 'attack tools' look like from a blue team perspective and what can you do to alert yourself of their use.
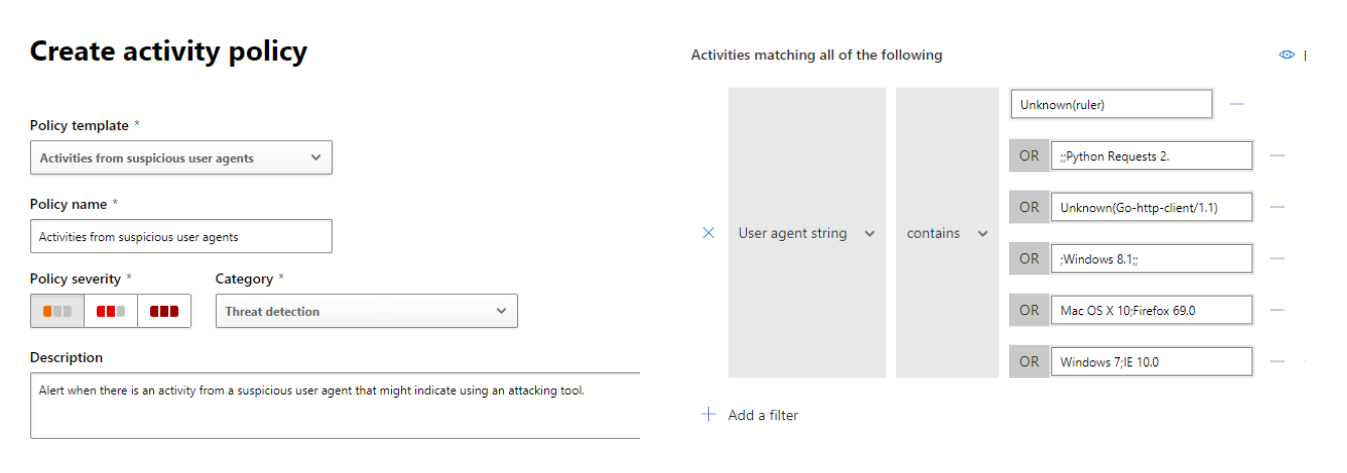
This blog lists the User Agents used by specific attack tools (in their default settings) as recorded in both the Security Center's Unified Audit Logs (UAL) and the Defender for Cloud Apps Activity Log.
BAV2ROPC
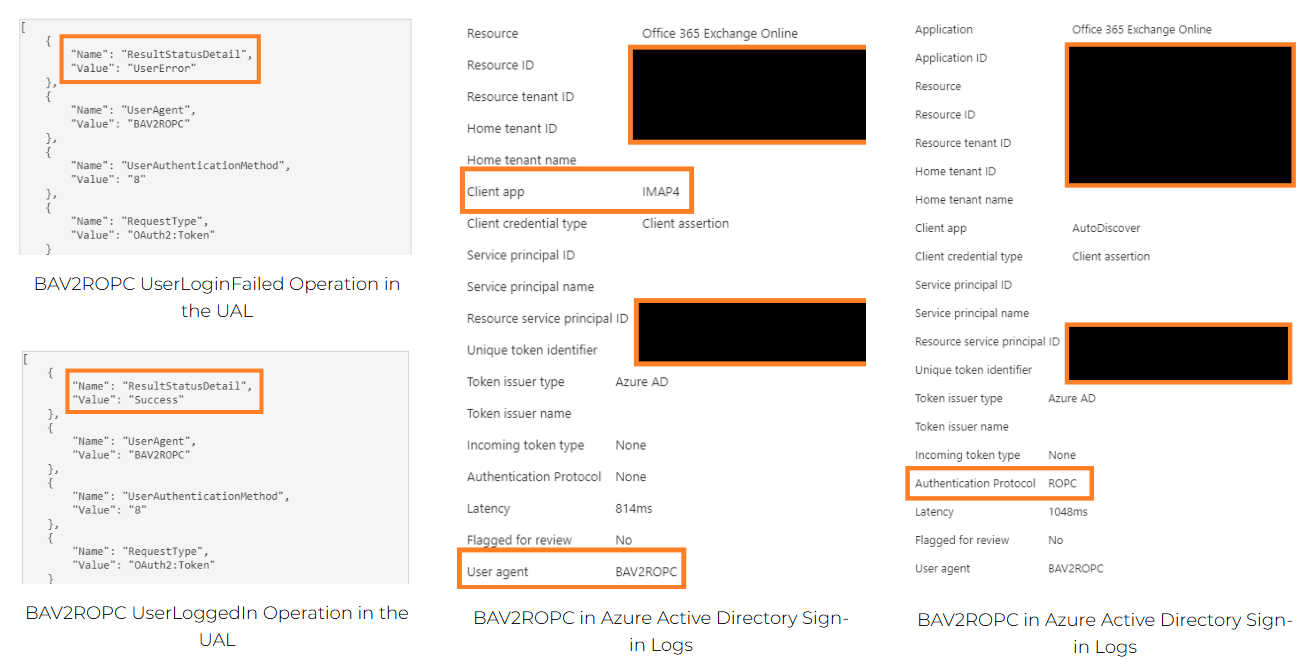
I have observed the User Agent "BAV2ROPC" in brute-force attempts and password spraying activity. BAV2ROPC's appearance is likely is determined by the use of legacy clients and authentication such as IMAP, and applied by Exchange regardless of attack tool.
Whilst I wasn't able to find any specific documentation for it, I figured BAV2ROPC is an acronym for "Basic Authentication Version OAuth2 Resource Owner Password Credentials".
It is worth noting though, the User Agent itself is not necessarily an indication of attack. From my experience the User Agent "BAV2ROPC" is also often noted for legitimate logons by legacy clients using legacy authentication (typically service accounts).
You should be able to identify pretty quickly if the authentication is legitimate or not through IP geolocation, reputation etc. but also be on the lookout for multiple 'UserLoginfailed' operations which are followed by a 'UserLoggedIn' operation involving the UserAgent.
See below for some screenshots of what BAV2ROPC authentication activity looks like in the UAL and Azure Active Directory Sign-In Logs.
'Passive' User Enumeration
Whilst not truly passive, some tools can enumerate users in a Microsoft 365 tenant without entering a password. This is done by looking at the codes returned by Microsoft infrastructure when entering a username.
When using these user enumeration techniques, as a password isn't entered the event is not recorded as a failed logon attempt in the tenant logs. This technique is used by tools such as O365Creeper but it can also be performed with BurpSuite.