Before anything else, preparation is the key to success
When organisations think about Incident Response (IR), they often imagine the dramatic moments: ransomware spreading, systems failing, executives on urgent calls, and security teams racing to contain the damage.
But the uncomfortable truth is this:
The outcome of a cyber incident is usually decided long before the incident ever happens.
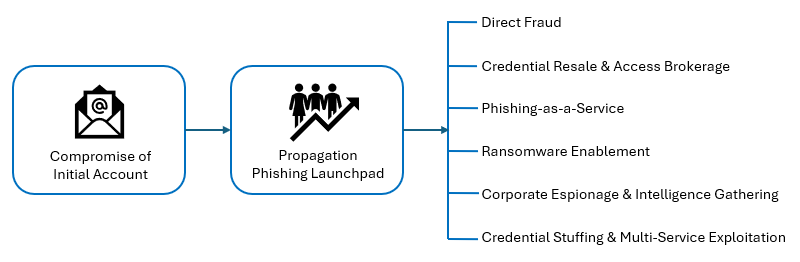
Credential Monetisation in BEC Attacks
Attackers targeting business email accounts have shifted from an instant-gratification model, to a ‘compromise-to-propagate’ approach. Why is this?
Cyber Assessment Framework - V4.0
On 6 August 2025, the UKs National Cyber Security Centre (NCSC) released V4.0 of its Cyber Assessment Framework(CAF). This followed the identification of a widening gap between the threats facing UK industry and the ability of our businesses to defend against them.
Direct Send - the direct threat within your Exchange Online configuration
HUNT-IR has recently observed several Business Email Compromise (BEC) cases in which attackers exploited the Direct Send feature of Exchange Online to deliver phishing emails directly to employees.
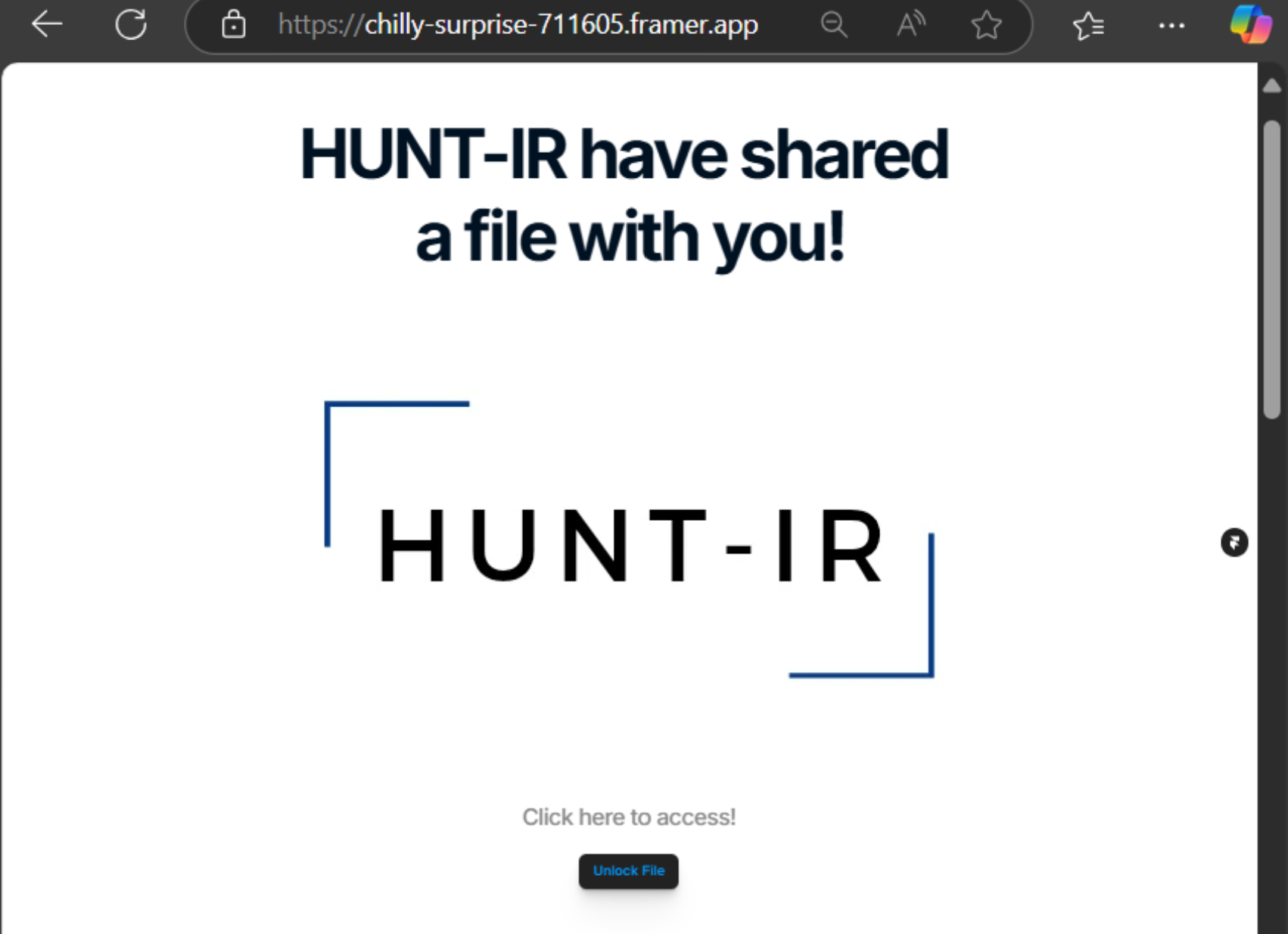
Phishing: You've been framed!
We take a look at how content creation site Framer can be used in phishing attacks to bypass email security filters, ultimately to facilitate Business Email Compromise (BEC) attacks.
Preparation Essentials
If you're reading this before an incident has occurred — well done. You're already ahead of the curve. The Preparation phase isn’t just a tick-box exercise; it’s your best shot at limiting damage before chaos strikes.
Forensics Blog: Adobe ConnectorIcons
Whilst investigating the root-cause of a Qakbot infection, HUNT-IR stumbled upon an undocumented file opening forensic artefact for Adobe Acrobat Reader.
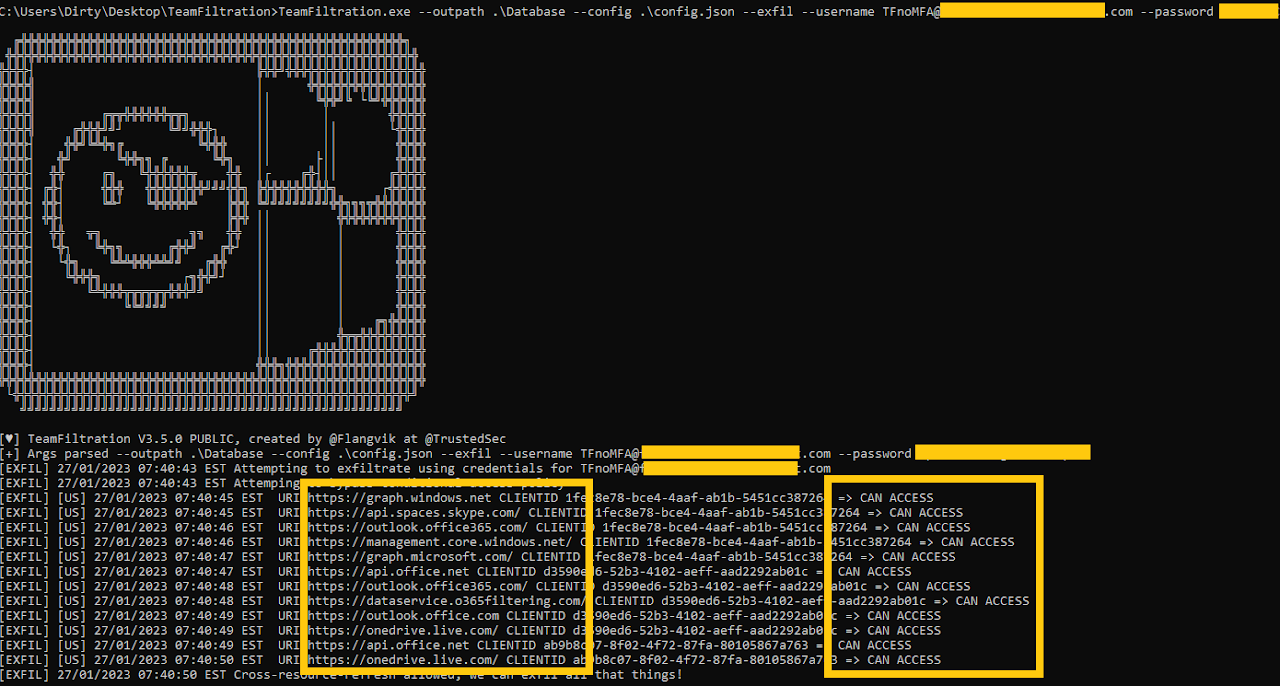
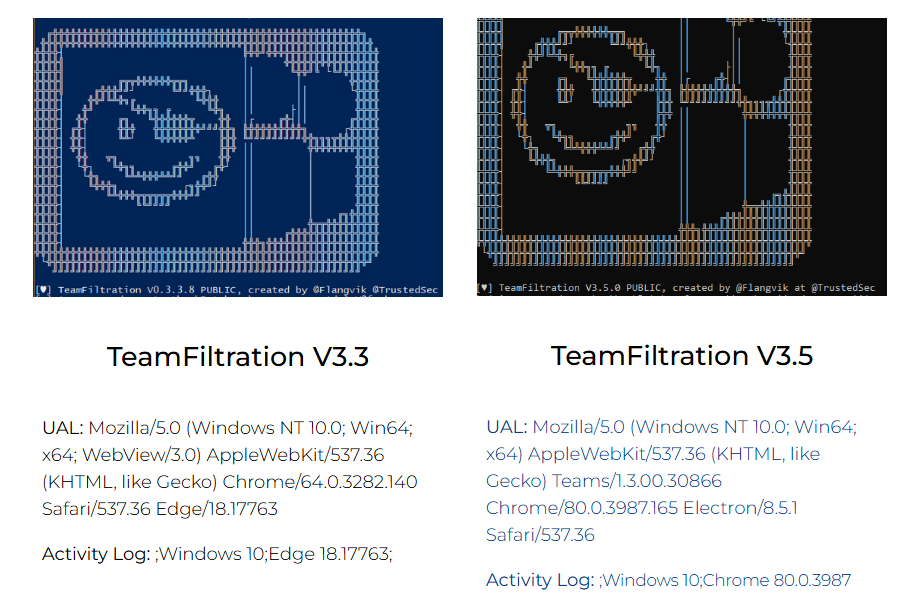
Teamfiltration vs MFA
TeamFiltration is a Microsoft 365 exploitation and post-exploitation framework which was publicly released on in August 2022 after it was presented at DEF CON 30. TeamFiltration allows penetration testers (and adversaries) to identify valid username and password combinations through enumeration and password spraying, which can then be used for account access and data exfiltration.
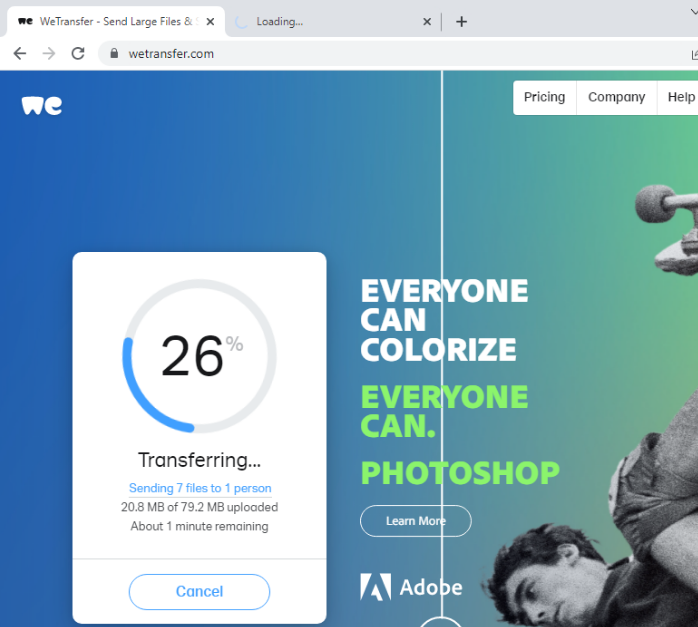
Forensics Blog: WeTransfer
WeTransfer is commonly used as a data exfiltration tool, and as such, we decided to take a look at how a digital forensic investigator could ‘put the user behind the keyboard’ by analysing the web browser history of the data transferor.
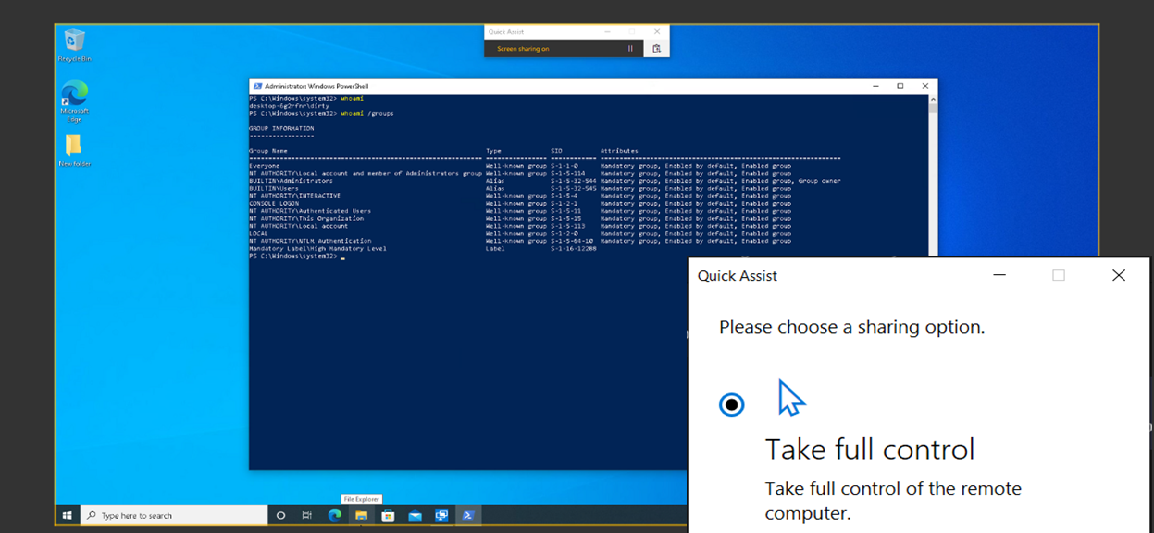
Forensics Blog: Quick Assist RAT?
Quick Assist is built on trust of the user ‘Giving Assistance’, and credit to Microsoft, it is an incredibly useful tool which enables Windows-savvy people to resolve the IT issues of family members or colleagues both directly and remotely. However, as with everything in IT, trust can be (and often is) misplaced, and can be (and often is) abused.
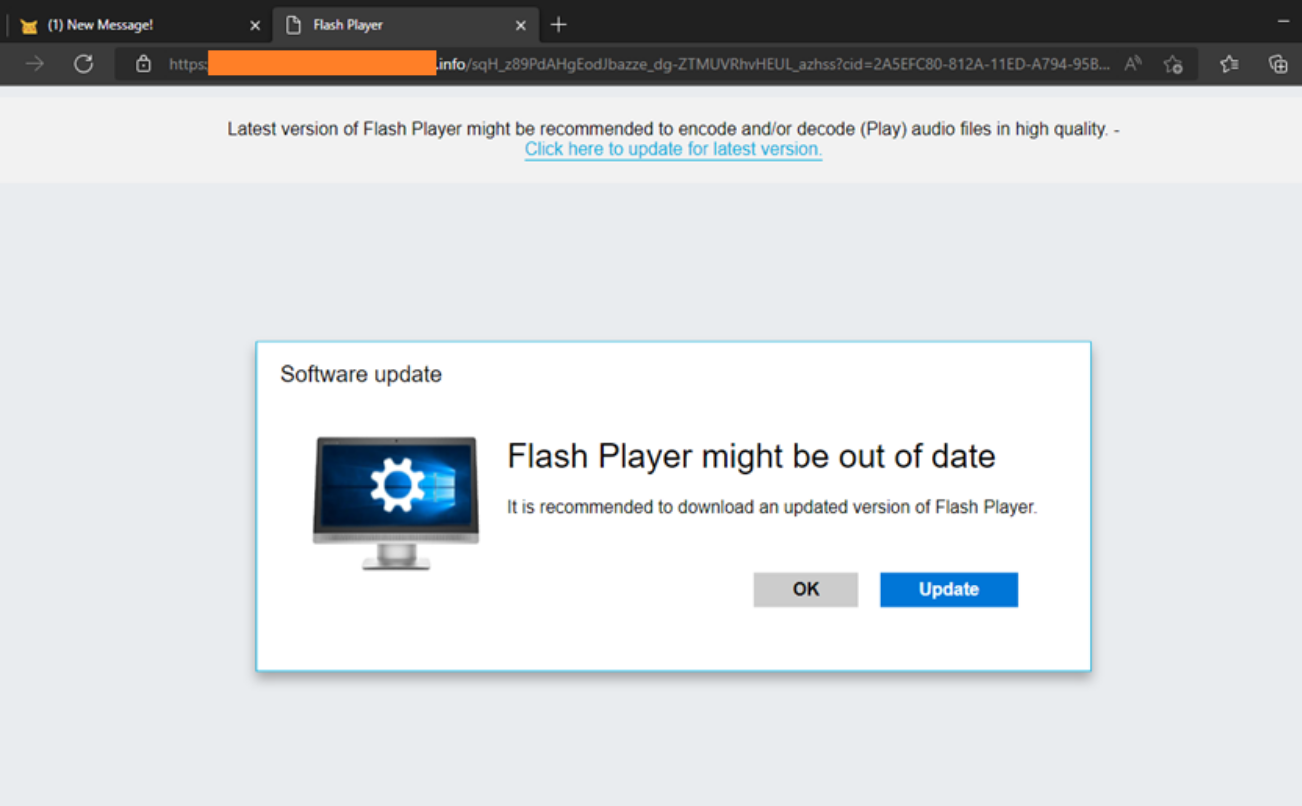
Forensics Blog: Unmasking Private Browsing
If you're anything like us, simply stating in your forensics report that "the malicious file was possibly (hopefully) downloaded by the user... maybe using a browser" simply won't do! So, keep reading to see how we set out to find the root cause of the infection using Microsoft's EDR solution.
Anatomy of an 'AiTM' MFA Bypass
A different 'flavour' of MFA bypass using an 'Adversary-in-The-Middle' (AiTM) or 'Man-in-The-Middle' (MiTM) methodology is becoming increasingly widespread whereby attackers are able to satisfy the MFA requirement with a stolen session cookie.
Microsoft 365: Attack Tool User Agents
There is no shortage of tools available for enumerating the users in a Microsoft 365 tenant (AKA Office365) and testing password security. But what do these 'attack tools' look like from a blue team perspective and what can you do to alert yourself of their use.
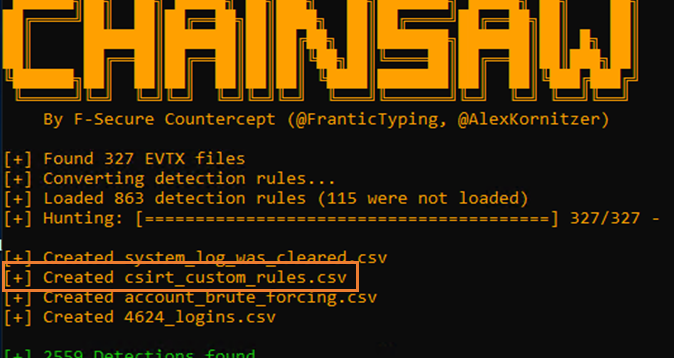
Hunting Blog: Creating Chainsaw Rules
Chainsaw is a powerful (and free) command-line tool created by F-Secure which in our experience is great for quick wins and providing start points in Windows endpoint investigations and Threat Hunts. Here’s how you can make your own detection rules.