Phishing: You've been framed!
Exploiting file-sharing platforms
Well-known cloud-based file-sharing platforms — such as Dropbox, Microsoft OneDrive, and Adobe Document Cloud — have long been exploited by attackers for phishing, using them to bypass email security filters, ultimately to facilitate Business Email Compromise (BEC) attacks.
These platforms are often used to host files that redirect victims to Adversary-in-the-Middle (AitM) infrastructure, where attackers proxy login pages for cloud-based business platforms like Microsoft 365 and Google Workspace.
Attackers are getting creative
During recent investigations, HUNT-IR has observed a growing trend of attackers abusing less conventional cloud collaboration and creative platforms. Services such as Figma, Reflect, Miro, Notion, Canva, Coda, and Framer have all observed being used to host pages containing malicious links.
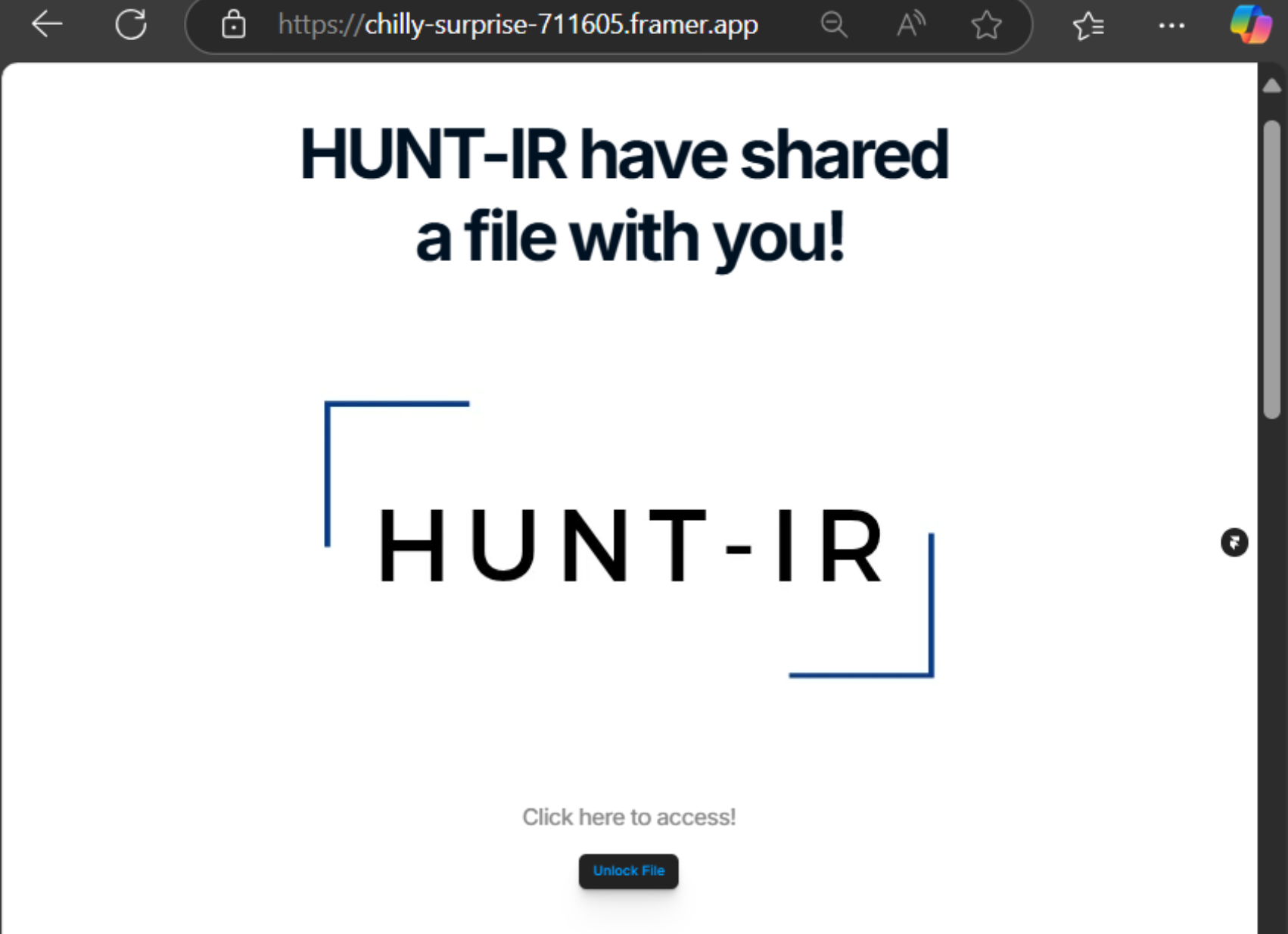
Framer in Frame
Picking on Framer, we decided to take it for a test drive to see just how easy it was to create a phishing site to share with the world.
We found that in just 5 minutes, we could go from account creation to publishing a credible phishing site!
Sign up: You can sign up to Framer for free, all you need is an email address. In the wild, HUNT-IR have seen attackers even use a compromised victim account for sign up!
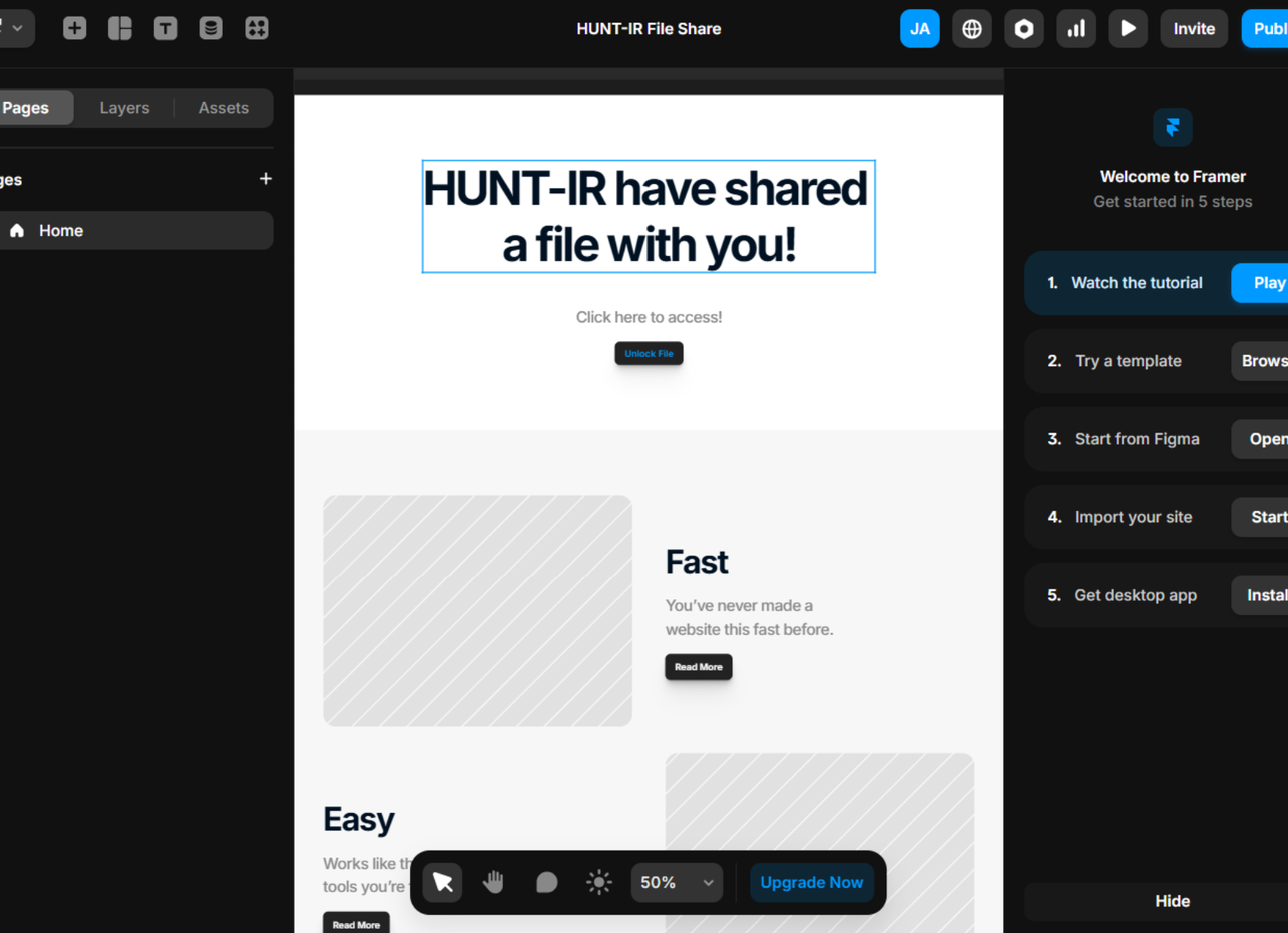
Site Creation: Credit to Framer, the site is really simple to use and has a bunch of professional looking templates to get you (or an attacker) started.
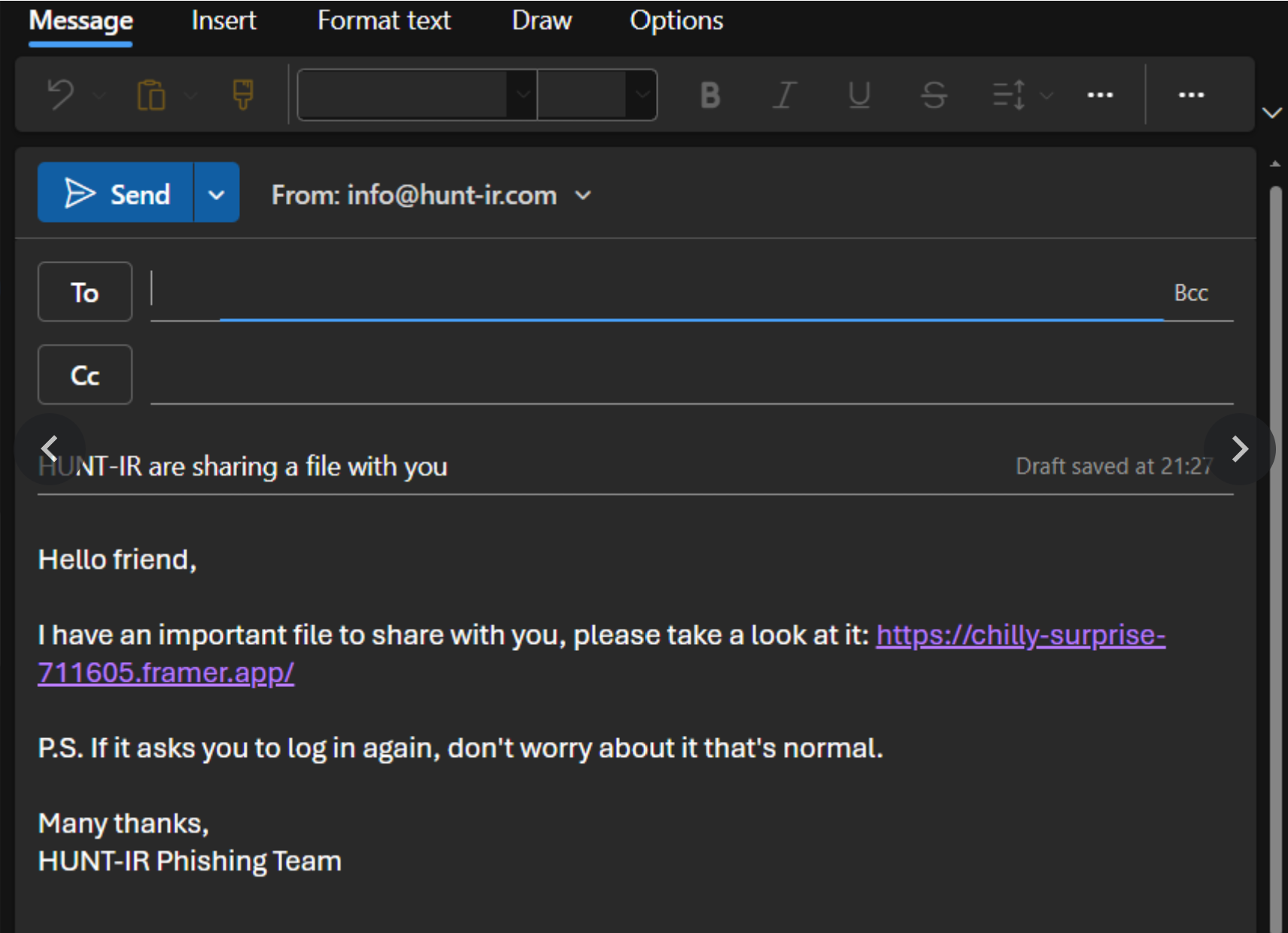
Publish: Once you've made your perfect phishing site, added your corporate logo and your malicious link, you are ready to publish! Hit the publish button and the site is live and accessible to anyone with the framer[.]app (or custom domain) url.
Distribution: Send your link far and wide via whatever means you choose!
Prepare to respond
With no shortage of file sharing and creative platforms on the market, attackers will always find a way to circumvent your email filtering.
As a technical control, rather than a whack-a-mole approach of blocking access to these types of platforms, HUNT-IR recommend defenders ensure they are using 'phishing-resistant' MFA (i.e. Authenticator App Passkeys or physical YubiKeys) to protect your user's accounts.
Beyond technical controls, you should prepare to respond, understand what your security gaps are, conduct a tenant review, test this scenario in a tabletop exercise, and of course, arm yourself with a Business Email Compromise Playbook as part of your tactical documentation.