Direct Send - the direct threat within your Exchange Online configuration
HUNT-IR has recently observed several Business Email Compromise (BEC) cases in which attackers exploited the Direct Send feature of Exchange Online to deliver phishing emails directly to employees.
What is Direct Send?
Direct Send is an SMTP relay method in Exchange Online that permits emails to be sent directly to a tenant’s mailboxes from on-premises devices, applications, or external cloud services using the organisation’s accepted domain. Because it requires no authentication, it effectively replicates anonymous inbound internet mail while appearing to originate from the organisation’s own domain.
How are attackers exploiting Direct Send?
By using Direct Send, attackers can bypass conventional email security controls—Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC)—because Direct Send, by design, does not validate these authentication protocols.
Attackers exploit predictable tenant naming conventions and common email formats, often leveraging tools like PowerShell to send convincing phishing messages. These emails appear to originate internally and frequently incorporate advanced social engineering tactics, such as AI-generated content or quishing (QR code phishing), to harvest user credentials or initiate fraudulent financial transactions.
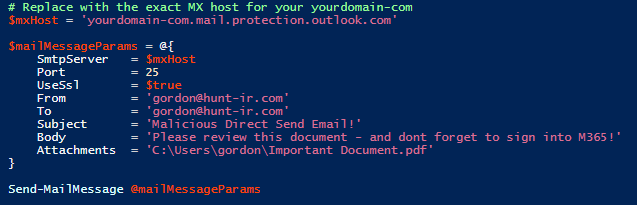
The screenshot below shows example PowerShell code crafted to send a phishing email via Direct Send:
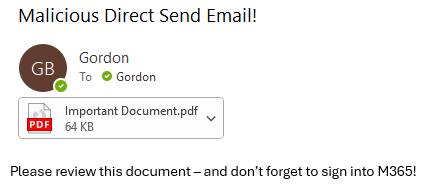
The next screenshot shows the example phishing email received by the victim. Noticed that it appears to have been sent from within the organisation. The sender address doesn't actually need to be valid, the attackers could have used something like 'media[@]hunt-ir[.]com' for example.
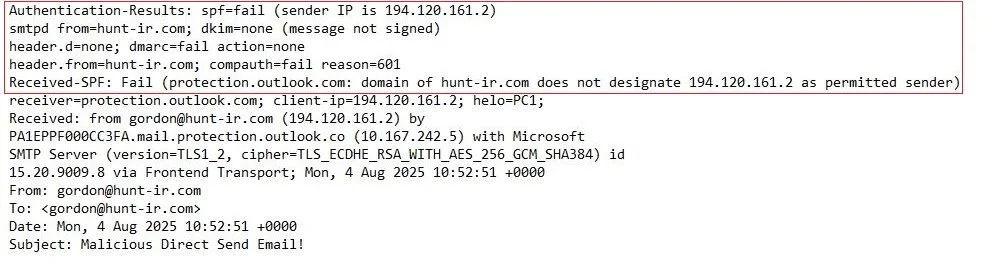
There will be no obvious tell-tale that Direct Send has been used, but if you look in the email header you will see that SPF, DMARC, and DKIM all fail.
Recommendations for Mitigating Direct Send Exploitation
Disable Direct Send where possible
By default, the Reject Direct Send setting is set to False. To enable the this feature, system admins can run the following PowerShell cmdlet:
Set-OrganizationConfig -RejectDirectSend $true
If unauthenticated internal email is required for business processes, migrate to authenticated SMTP client submission or SMTP relay with strict IP-based connectors.
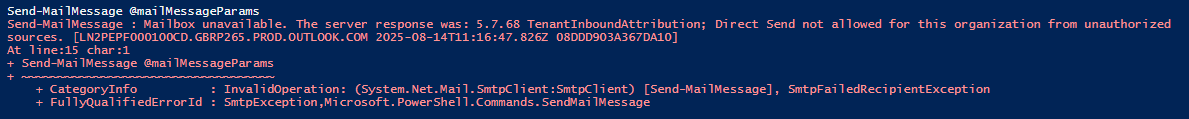
Once the Reject Direct Send setting was set to True, HUNT-IR noticed the following message during testing when attempting to send a Direct Send mail using PowerShell:
If disabling Direct Send is not possible
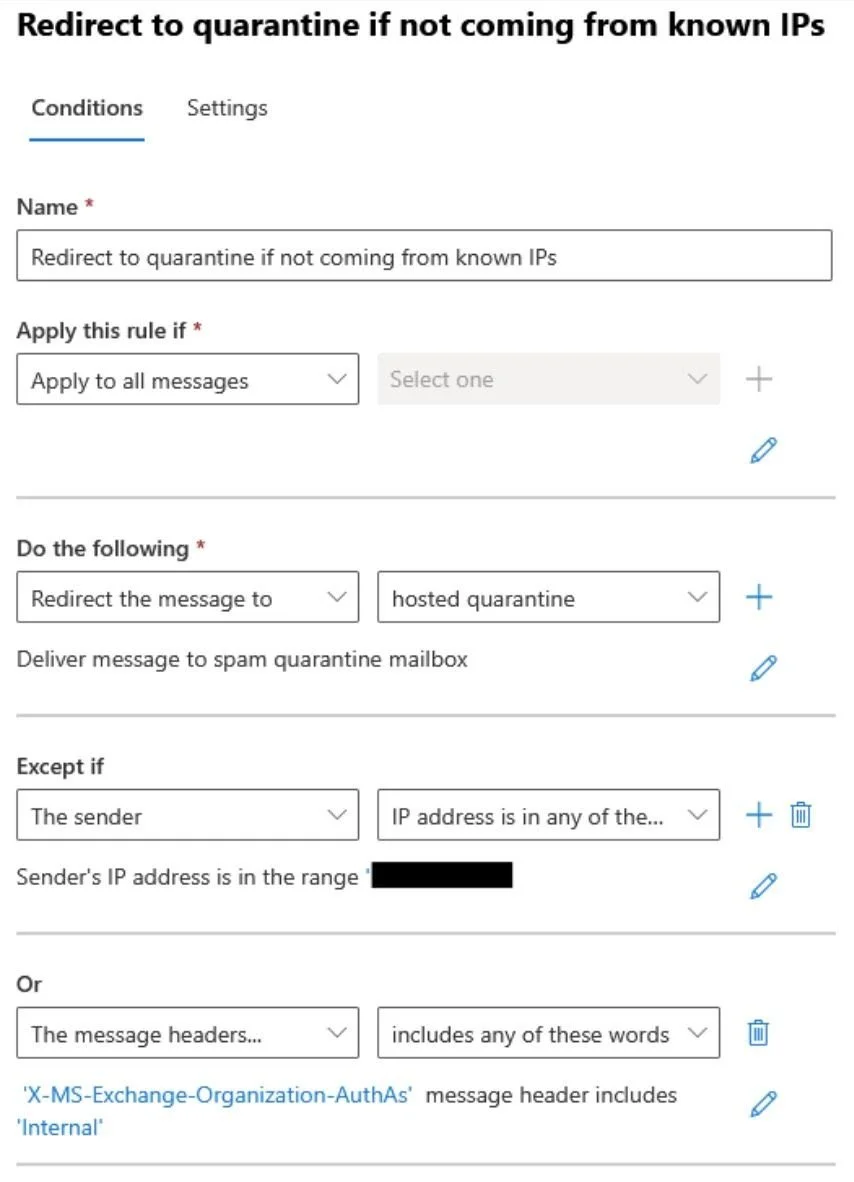
If you can’t enable Reject Direct Send, due to business reasons, you can reduce risk by creating a high-priority mail flow (transport) rule that quarantines any inbound mail not originating from your approved IPs (MX records, on-premises servers, or other authorized senders).
Priority: Set to 0 and enable Stop processing more rules.
Action: Quarantine the message.
Exceptions: Allow messages from approved IPs or those with the X-MS-Exchange-Organization-AuthAs header containing Internal.
OR
'X-MS-Exchange-Organization-AuthAs' header contains ''Internal''
Source: Direct Send vs sending directly to an Exchange Online tenant | Microsoft Community Hub
The following PowerShell command can be used to implement such a rule:
New-TransportRule -Name "Redirect to quarantine if not coming from known IPs" -Quarantine $true -ExceptIfHeaderContainsMessageHeader 'X-MS-Exchange-Organization-AuthAs' -ExceptIfHeaderContainsWords 'Internal' –ExceptIfSenderIpRanges ‘MX records + on-premises IPs + other authorized IPs ' -StopRuleProcessing $true -Priority 0
Recommendations for Email Security Hardening
Harden email authentication
Enforce strict DMARC policies (p=reject).
Configure SPF with a hard fail (-all).
These controls help prevent domain spoofing from external sources.
Mandate Multi-Factor Authentication (MFA)
Enforce MFA on all Microsoft 365 accounts to protect against credential theft, even if phishing succeeds.
Deploy advanced email security solutions
Use reputable email security tools, e.g. Microsoft Defender for Office 365, that provide anti-impersonation, behavioural analysis, and threat intelligence.
Enhance user security awareness
Deliver targeted, ongoing training on modern phishing tactics—including AI-driven content and QR code attacks. Encourage users to report any suspicious messages, even if they appear internal.
Strengthen monitoring and forensics
Implement comprehensive logging and monitoring across M365. Correlate sign-in logs, audit logs, and mail flow data to detect anomalies and identify subtle attack patterns.
Enforce strong internal controls for sensitive transactions
Require multi-level approval and out-of-band verification for financial transfers and sensitive data requests, even if they appear to come from trusted accounts.
Conclusion
The threat of Direct Send abuse in BEC attacks highlights that cloud security is not just about patching vulnerabilities—it’s about hardening configurations and understanding how legitimate features can be misused. A vigilant, adaptive security posture is essential to defend against these increasingly sophisticated attacks.