Credential Monetisation in BEC Attacks
Introduction
Do you remember when attackers used to try and convince your finance department to pay an invoice to a dodgy bank account – its been a while, right?
Attackers targeting business email accounts have shifted from an instant-gratification model, to a ‘compromise-to-propagate’ approach. For some time now attackers have been using compromised accounts to launch mass phishing campaigns, rather than for direct fraud. Why is this?
Now acting as 'access brokers', they are bulk selling compromised business email credentials on the dark web. These can then be acquired by other threat actor groups to be used as part of more complex attacks. It is likely that this has become a more stable crime economy for criminals specialising in BEC attacks.
The ‘Compromise-to-Propagate’ Workflow
Initial Breach: The victim’s email account is compromised via phishing, often sent from a trusted business contact who was previously breached. Attackers leverage legitimate file-sharing platforms such as DocuSign or SharePoint to host malicious files, which redirect the victim to a proxied login page that harvests credentials. See our Prepare to Respond - M365 'AiTM' blog to understand how this works.
Phishing Launchpad: The compromised mailbox is used to send more phishing emails, abusing its inherent trust and reputation. This stage is often the first point at which our clients notice that one (or several) of their email accounts have been compromised.
Harvest & Expand: Fresh victim credentials are harvested from newly compromised internal and external accounts.
Monetisation Pathways: The compromised credentials are then sold or traded – before the account gets disabled.
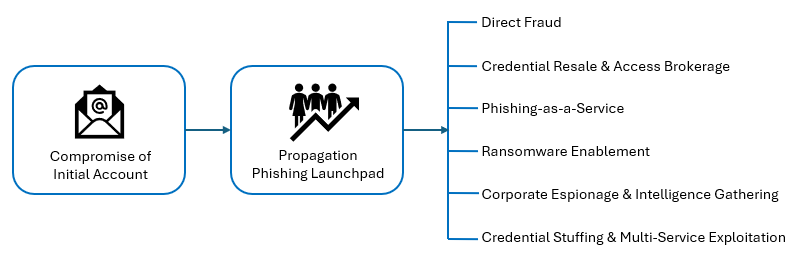
Monetisation Pathways
Stolen Credential Monetisation Pathways
Once attackers have harvested fresh credentials from the targeted account, they face a choice: exploit them directly, or sell them into the underground marketplace. Today, the latter often dominates, but there are multiple pathways for monetisation:
1. Direct Fraud (Old School BEC)
Although less common than a few years ago, attackers still attempt classic fraud — invoice redirection, payroll diversion, or fake C-Suite requests. These attacks are risky and noisy, but a single success can net large sums.
2. Credential Resale & Access Brokerage
Increasingly, compromised accounts are packaged up in bulk and sold on dark web forums or private Telegram channels. Prices are low (often under £20 per credential), but volume makes it profitable. This model allows attackers to scale, creating a steady revenue stream rather than gambling on one big payout.
3. Phishing-as-a-Service
A compromised mailbox carries inherent trust and reputation, making it a perfect launchpad for large-scale phishing. Access brokers may lease or resell accounts specifically for use as spam relays — either to spread credential-harvesting phishing, or to distribute malware designed to establish initial footholds on victim networks.
4. Corporate Espionage & Intelligence Gathering
Email accounts contain sensitive information: deal negotiations, supplier contracts, technical documentation, even intellectual property. Some attackers monetise by selling this data directly, or by tipping off competitors. While harder to monetise quickly, this path is attractive to well-resourced threat actors.
5. Ransomware Enablement
Perhaps the most dangerous pathway: email access is sold to ransomware affiliates who use it as a foothold. Once inside, they pivot via single sign-on (SSO) or VPN access, escalate privileges, and deploy ransomware across the environment. In this sense, what starts as “just a compromised mailbox” can escalate into a full-blown enterprise breach.
6. Credential Stuffing & Multi-Service Exploitation
Since many users reuse passwords, stolen email credentials often unlock other systems — from SaaS apps to VPNs to banking portals. Attackers test credentials across multiple services, broadening their access and monetisation options.